1. Overview
3. Requirements of ATM security system
4. Implementing security services on ATM
5. Conclusion
In recent years, security has been more and more significant in network environment with the emergence of the internetworking technology. The internetworking technology can provide the communication channels across networks so that machines in different networks can talk to each other. However, the internetworking communication will be exposed to all kinds of attacks in such an open environment. Most of the network technologies, without integrating with security mechanism originally, have to be redesigned to provide some security services. ATM is one of those technologies.
ATM stands for Asynchronous Transfer Mode. Originally, it is a transfer mode to implement the B-ISDN(Broadband Integrated Services Digital Network) technology so that all forms of data traffic(voice, video, data etc.) can be transferred over telecommunication networks. But ATM is not restricted to B-ISDN. It has been used to provide a simplified network infrastructure for various network connections, e.g. LAN, MAN or WAN. ATM is a connection-oriented technique. In ATM, hosts are connected by a network of switches. When two parties want to talk, they request a Virtual Channel from the switch network first. Then the two parties can send data to each other. Although the communication parties can send data in any size, ATM always delivers data in a fixed size unit, which is called a cell. A cell has 5 octet header and 48 octet payload. Cell switching will base on the 5 octet header. In the way, a cell can go through a switch very quickly. To meet different requirements of specific traffic, ATM also introduces the concept of Quality of Service(QoS). Details about ATM technology can be found in any ATM textbooks[ CL95, DL95]. And the most recent advances in this area can be found in discussions and contributions of ATM Forum, which is the standards organization for ATM.
In fact, issues in ATM security have not gained enough attention until 1995, when a group within ATM Forumwas established to address the security issues. Therefore, compared with other security area, ATM security is still in its beginning. In this paper, we first examine the threats to ATM networks. And then we discuss the requirements of ATM security. In section 4 we are going to discuss the implementation issues of ATM security. Phase I ATM Security Specification has been discussed in this section. In conclusion, we discuss some examples of the ATM security products.
As other networks, ATM networks will suffer a lot of threats[ LPR97, Hanson95, Chuang96, Deng95, KB96, TF95]. Typical ones are eavesdropping, spoofing, service denial, VC stealing and traffic analysis etc. Notice that VC stealing and traffic analysis happen only in ATM networks.
Eavesdropping refers to the threat that the attacker connects or taps into the transmission media and gain unauthorized access to the data. It is one of the most common attacks to the network. Since most ATM networks are connected with optic cables, some people might get the wrong impression that is not so easy to tap a ATM network. However, Bacon [ BACON] reported that depending on the tapping point, equipment to tap a fiber optic cable costs about $2,000, which is affordable for almost any individual. Although a hacker has to be familiar with the communication technology and relevant protocols operating at the tapping point, this information is widely available in academic environment. For instance, any member of ATM forum can access to the contributions and specification about ATM architectures and ATM security. And also there are a lot of homepages relative to these topics. As the technology become matured, standards will be established and the technology will be well-known, nothing will be protected by keeping the document secret.
Spoofing attack means that an attacker tries to impersonate another user to the third part therefore can get access to resources belonging to the victim to take advantages or just destroy them. Spoofing might need special tools to manipulate the protocol data unit. And sometimes it might require the attacker has special access permission, say, must be the super user in UNIX environment. However, since a network will be connected to many untrusted networks via the Internet, it's impossible to prevent a hacker from getting this access permission or even trace the people with this particular access permission. ATM is being implemented in public domain. Therefore, it is subject to this kind of attack also.
ATM is a connection-oriented technique. A connection, which is called Virtual Circuit(VC) in ATM, is managed by a set of signals. VC is established by SETUP signals and can be disconnected by RELEASE or DROP PARTY signals. If an attacker sends RELEASE or DROP PARTY signal to any intermediate switch on the way of a VC, then the VC will be disconnected[ SHB95]. By sending these signals frequently, the attacker can greatly disturb the communication between one user to another, therefore will disable the Quality of Service(QoS) in ATM. Combining this technique with other tricks like eavesdropping, the attacker can even completely block one user from another.
If two switches in an ATM network compromise, the attacker can even steal a VC from another user. Say VC1 and VC2 are two virtual channels which will go through switch A and switch B. VC1 is owned by user U1 and VC2 is owned user U2. If A and B have compromised, then A can switch VC1's cells going from A to B through VC2 and B will switch back those cells to VC1. Since switches will forward cells based on the VCI(Virtual Channel Identifier) or VPI(Virtual Path Identifier) in the cell header, A and B can just alter these fields back and forth. Switches between A and B won't notice these changes and will switch the assumed VC2's cells just like the authentic VC2's cells. In public packet-switching network, U1 won't gain too much by this trick. However, in ATM network, if quality of service is guaranteed, then user 1 can gain a lot by stealing a higher quality channel which user 1 is not entitled to use according to the access control policy. User 1 can gain even more if every user has to pay for the communication. In both cases, user 2 will be hurt. Someone maybe argues that the possibility that the switches will compromise is pretty low. That will true if the ATM network is owned by one organization. However, as mentioned by Alles[ ALLES95], when we consider ATM internetworking, in which case cells will travel through different ATM networks, it will be very easy for two switches to compromise.
Traffic analysis[ TF95] refers to a threat that the hacker can get information by collecting and analyzing the information like the volume, timing and the communication parties of a VC. Volume and timing can reveal a lot of information to the hacker even though the data is encrypted, because encryption won't affect the volume and timing of information. And also the source and destination parties can be obtained from the cell header (normally is in clear text) and some knowledge about the routing table. Another related threat is called convert channels. In this technique, the attacker can encode the information in the timing and volume of data, VCI, or even session key to release information to another people without being monitored. Normally, these two attack won't happen. However, when ATM is used in a environment requiring stringent security, it might happen.
To build an ATM security system, the first thing we should do is to identify the requirements of securing communication over ATM. This issue has been discussed widely in ATM Forum[ MH95, SPEC97, FRWK97] and literature[ TF95, SHBW96, KB96, Deng95]. In this section, we are going to talk about general requirements for network security system, and then we will discuss the first draft of ATM security framework, which has summarized the recent results for this topic in ATM Forum contributions.
When we talk about the network security, the following requirement has to be considered:
It's proved that besides non-repudiation, a secure public network at least has to meet the other three requirements. And a security system for a network also has to provide a secure key management(e.g. key distribution) services and user access control.
A good key management scheme are the foundation of a security system. Security comes from the encryption/decryption. If the keys used in encryption/decryption can be easily obtained by an attacker, then the security system will be defeated. And in a network system, because there are some many users, key management and distribution can no longer be done manually, it has to be done automatically or half automatically and key exchange will go through the network. How to secure the keys when they are transferred over the network, especially when the network is setup, is a big issue.
Authentication is important in communication system. In a public network, everything, even the keys, has to be authenticated to prevent spoofing. Confidentiality is not only required to keep the data from unauthorized access, but also can guarantee the correctness of distribution of symmetric key. Integrity can be viewed as some kind of authentication, which means the data should the original data sent by the one who claims it (without tampering). Key management, authentication, confidentiality and integrity depend on each other. Flaws in any of them will make the system insecure.
Access control is more significant in ATM networks than in other networks. ATM networks guarantee the quality of services(QoS) of communication. QoS is implemented by classifying the traffic into different classes and route them in different priorities. If the access to the network is unrestricted, then it turns out nothing can be done about QoS.
For more details and discussion about these concepts, the reader can refer to recent data security texts as [ CLS89, MP93, SP89].
People have practiced security for a long time. In the past, security services were considered only after the network service was totally designed. These ad hoc approaches turn out to be unsatisfactory. ATM Forum tries to avoid such pitfalls by considering the security as one integrated part of ATM.
Recently, ATM Forum Security Working Group proposes a draft of Security Framework for ATM[ FRWK97] to address the basic requirements for ATM security. The framework is originally proposed by Klasen, Munzert and Nauer[ KMN971] in February 1997. Based on the analysis of the objectives from the customer side, operator side and public community side, the draft identifies the main security objectives for ATM security:
Confidentiality and data integrity are obvious. Accountability means that all ATM network service invocations and network management activities should accountable. And any entity should be responsible for the actions it initiates. Accountability includes both authentication and non-repudiation. It is extremely important for operators to manage the system and bill the services. Availability means all legitimate entities should be able to access to ATM facilities correctly, no service denial should happen. That is important for QoS operation.
According to these main objectives, the draft proposes the principal functions which a ATM security system should provide:
Among the ten requirements, the last two won't provide security services. However, they are necessary to support the maintenance of security services. If the security system can not be recovered from attacks and can not provide security services any more, then the system won't be secure after these attacks. On the other hand, security services and the information about security have to be managed securely. They are the foundations of the security system.
The draft also includes how to interpret the functional requirements for user plane to the specific ATM instances (the interpretation first appears in [ KMN972]). Interpretation about the functional requirements for control plane can be found in [ KM97]. However, they don't include too many details. Actually, different instances of ATM network will have different concerns about the threats therefore will emphasize on different objectives. A framework should be abstract enough so that can provide a guideline to different ATM instances. The security working group will finish the mapping of the security services to ATM network architecture and identification of the mechanisms and algorithms to implement the security service in the future. But whatever they will come up finally, it should be flexible enough to fit in different ATM network instances.
After we identify the requirements of a ATM security system, we will discuss how to implement security services on ATM network. In this section, we first examine the architecture of ATM and identify the ATM security scope. And then we are going to discuss how to place the security services in ATM architecture. After that, we will discuss the current draft of Phase I Security Specification 01-03, which is proposed by ATM Forum. And then we survey some new comments and suggestions which are not included in the current draft of Phase I Security Specification. At last, we discuss some challenges for implementing ATM security services.

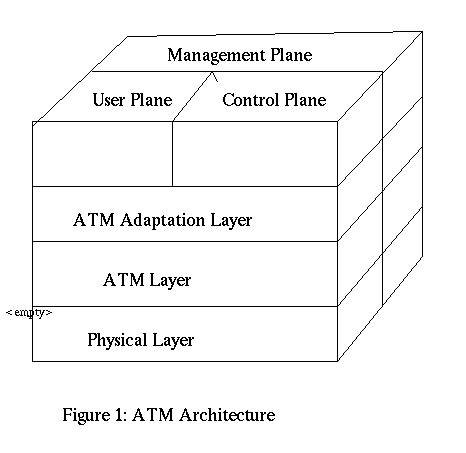
To identify ATM security scope, let's first look at the architecture of ATM. ATM architecture (figure 1) includes three planes:
A plane includes entities. Entities in user plane are used to transfer user data. While the entities in control plane will deal with connection establishment, release and other connection functions. And the management plane entities perform management and coordination functions related to both the user plane and the control plane. In particular, the management plane includes the PNNI functions related to establishment of a routing infrastructure. Besides entities in these three planes, there are ATM layer entities. The ATM layer entities perform ATM data transfer on behalf of the other entities in the three planes. Figure 2 shows the interaction of all the entities.
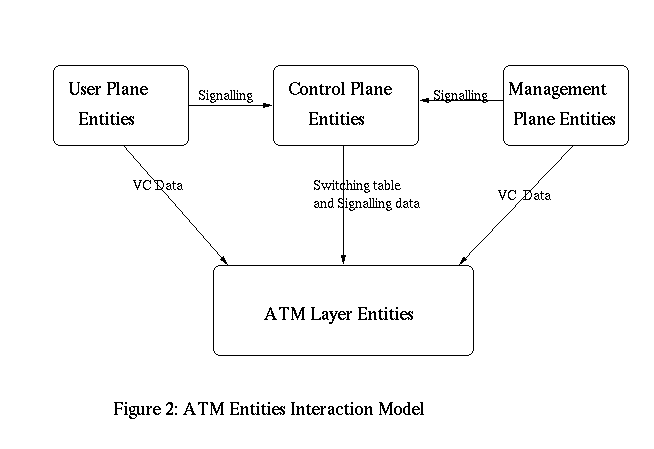
It's obvious that to implement the security requirements in ATM networks, all the three planes and the ATM layer have to be included into the scope.
After we identify the requirements and scope of ATM security, now we will discuss how to put the security services in the ATM network architecture.
According to figure 2, user plane is the plane that directly interact with user. Therefore to meet the user's security objectives, user plane has to provide security services like access control, authentication, data confidentiality and integrity. Other services like key exchange, certification infrastructure and negotiation of security options might be useful to meet the variety of the customers' requirements. Therefore they also should be supported by user plane[ SPEC97]. Note that providing different security services options is important because of the various traffic classes in ATM network. Different connections have different security requirements. User plane security services have to provide enough flexibility to meet these requirements.
In ATM Control plane will configure the network to provide communication channel for a user. From figure 2, we can see control plane can interact with the switching table, or to manage the virtual channel. Several attacks mentioned in section 2 are relative to control plane. Therefore, it is very important to secure control panel. The key point to secure control plane may be to provide authentication and confidentiality of signal[ SPEC97]. If the message recipient or even the third party can verify the source of this message, then denial of service attack can not happen. And Control plane authentication could also be used to provide the auditing information for accurate billing which should be immune to repudiation.
Management plane security is also important. Chuang[ Chuang96] has suggested that management plane security scheme at least should consider the following items: Bootstrapping security, authenticated neighbor discovery, the Interim Local Management Interface security and permanent virtual circuit security. And in security framework, we have to provide security recovery and security management. The major parts of these two requirements seem have to be implemented in management plane.
Since all data have to be transmitted through ATM layer, the security of ATM layer is extremely important. As pointed out by Peyravian and Herreweghen[ MH95], authentication, confidentiality and integrity are also required in the ATM layer. ATM layer security has to be implemented on end-to-end(ATM endpoint to ATM endpoint), edge to edge (border ATM switch to border ATM switch) and ATM end point to switches basis[ MH95]. Here, data integrity is a tricky thing. Since the switches can see and forward ATM cells, data integrity for edge-to-edge and ATM endpoint to switches is better to be implemented on a per-ATM-cell basis. That means we have to include a signature to each cell. That will introduce a unwanted overhead. Therefore, Peyravian and Herreweghen[ MH95] suggest that integrity only be provided on an endpoint to endpoint basis.
It should be aware that endpoint to endpoint security in ATM layer is different from the security in higher layer[ MH95]. An ATM layer connection is not the same as a higher layer connection. Therefore although a ATM connection is authenticated and secure, higher layer connection still should be authenticated and protected. This is necessary especially when a connection is set up for a legacy network which is connected to a ATM switch. In this case, the connection will be shared by all hosts on the legacy network. Actually, the security issue of this scenario is still untouched yet.
To solve the security problem for ATM security, ATM Forum Security Working Group is working on an ATM security infrastructure. Their efforts end up with Phase I Security Specification[ SPEC97]. Until now, they have come up with the third draft (01-03).
Current draft of Phase I Security Specification deals mainly with the security mechanisms in user plane and a part of control plane. It includes mechanisms for authentication, confidentiality, data integrity and access control for the user plane. It also includes mechanisms for authentication for the control plane. Management plane and the rest of control plane have not been touched yet. The specification also specifies some supportive security services: negotiation of security services and parameters. Note that the specification just specifies the mechanisms which must be implemented in the ATM layer and/or AAL(ATM Adaptation Layer)[ SPEC97].
The goal of Phase I Security Specification is to provide a flexible enough infrastructure so that it can accommodate different algorithms and key lengths, provide interoperability across vendors, provide compatibility ATM devices without security extension, and provide separability of authentication and integrity from confidentiality. The infrastructure also has to be scalable to a large number users, compatible across successive versions of specifications.
User plane security in the Phase I Security Specification is applied on a per VC basis. The security services will be supported in point-to-point and point-to-multipoint fashion. At the ends of a VC or along the path of VC, there will be Security Agents (SAs [ Bullard97]). The security will be implemented between security agents.
In user plane security, access control is used to prevent unauthorized party to establish connections. To make the specification independent from any implementation, the Phase I Specification standardizes the information and the information exchange mechanism required by a specific access control algorithm. Authentication is used to make sure that the calling and called parties are indeed genuine. Authentication is the first step of the communication. In the specification, authentication is done via cryptographic techniques with symmetric or asymmetric key algorithms. According to the specification, data confidentiality mechanism is on per cell basis. Payload of a cell will be encrypted so that it won't be accessed by unauthorized user. Notice that the encryptor won't encrypt or change the cell header. Data integrity is separated from the data confidentiality in the phase I Specification. This separation allows the data integrity services to be implemented at the AAL Service Data Unit(SDU) level. For each AAL-SDU unit, a signature is computed and attached to the ALL-SDU so that the receiver can check whether or not the data are corrupted. Data integrity has two options. One provides replay/reordering protection while another does not. The difference in implementation is that for option with replay/reordering protection, a sequence number is attached to the AAL-SDU before the calculation of the the signature therefore the signature will protect both the data and sequence number. Therefore the receiver can discard an old AAL-SDU based on the sequence number attached to AAL-SDU.
Control plane security currently just provides a signaling authentication mechanism which will bind an ATM signaling message to its source. This binding can be used to verify the message is from the source it claims to be by the receiver or the third parties. This can protect ATM network from such attacks like service denial which will manipulate the signals. Signaling authentication is also significant to accurate billing. Notice that authentication for the control plane is different from authentication in user plane because a signaling message has both end-to-end and hop-by-hop significance. A signaling message will be processed by each switch on the way. Therefore hop-by-hop authentication is necessary. In current draft of the specification, the authentication of control plane is till not finished yet.
Compared to the work about security of user plane and control plane, support services are more mature in current draft of the specification. The following issues has been addressed:
These services provide a basis for the ATM security system. The Phase I Security Specification has specified how to apply the existing algorithm to implement the these services.
Phase I Security Specification 01.03 has addressed a lot of issues in ATM security. However, compared with what we expect in the security framework, the achievement is far from success. A lot of comments and suggestions have been made.
First issue is about the security of management plane. Management plane is not included in the scope of Phase I Security Specification. As pointed out by Bogler et al[ BNM97], Phase I Security Specification should include some basic management requirements and managed entities for ATM security. Otherwise interoperability will be confined to user and control plane. Being aware of that, they propose a protocol independent MIB for the management of ATM security services[ BMN97]. However, their scheme doesn't cover all the aspects of security management. Two other important issues, ATM system security management and security of ATM network management, are not addressed in their proposal at all.
Realizing the importance of the security of ATM network management, Przygieda and Bullard[ PB971] proposed a mechanism for PNNI peer authentication and cryptographic data integrity, which was accepted in ATM Forum Chicago meeting and developed into baseline text[ PB972] later. In their proposal, they identify two kinds of threats to PNNI: 1) "Unauthorized introduction of routing information"; 2) "Unauthorized modification of routing information". Under this circumstance, authentication and integrity are the most important requiremnts. To provide strong authentication between peer entities, they introduce a PNNI certification hierarchy. In this hierarchy, a peer has to present a credetials which has been certified by an authority to the ones it wants to speak to. After authentication is finished, the peers can exchange session keys which they can use to protect the integrity of the later messages. After that, peers can talk to each other safely. Notice that this proposal doesn't slove all the security problems for PNNI. For example, if a trusted PNNI peer entity introduces inappropriate information, then there is no way to provent it.
Another suggestion is about negotiation of algorithms for security services. In current draft of Phase I ATM Security Specification, only a primary and an alternate algorithms are available to select for each security service. Hebda, Shields and Kubic point out that it's desirable to allow more than two algorithm choices to be selected for any security service[ HSK97]. Therefore, they propose a scheme that an initiator can give a list algorithms and the responder can select one from it based on its capabilities and the priorities of the list of algorithm. By this way, the negotiation of algorithms will be quite flexible, although it might result in choosing an unexpected combinations of algorithms for a set of security services[ HSK97].
As mentioned above, even authentication of control plane is not finished in current draft of Phase I Security Specification. A suggestion has been made by Shields et al[ SKH97]. In their proposal, user plane data integrity will be used to provide hop-by-hop authentication of signaling messages.That is, a keyed hash function will be computed over the AAL5 SDU as the signature. Each authenticated link has an agree-upon algorithm and key(s). Notice that control plane authentication can not use two- or three- way exchange protocol because the signals have to be verified when they traverse in the network.
When ATM technology is used in wireless communication, unique security problems will arise [ CF97]. These will introduce a set of mobile specific security requirements[ BW96] into ATM security. Therefore Bautz and Wrona[ BW97] suggest that security for wireless ATM should be include in the future version of security specification.
In next section, we are going to look at what makes it so difficult to implement.
At the first glimpse, ATM security should not be too difficult to implement since we have a various security practices in other fields. However, ATM security is very difficult to implement. ATM switch is a high speed cell multiplexer and ATM network is a connection-oriented network. These properties will bring some unique problems when we try to secure the ATM communication. In this section we will present some challenges in implementation of ATM security mechanism, most of them can be seen in [ Chuang96].
It is clear that encryption is the basis for a lot of security problems. In ATM security, encryption will happen in two level. One level is the application level. There won't be any problem with it since we can apply any security mechanism. Another level is the ATM layer level. In this level, we are going to deploy security mechanism to a switch. Since switch see and forward only cells, we have to apply security mechanism to a cell. That can not be totally avoided in ATM network. For example, if we want to provide integrity and confidentiality services to the cell header, or if we want to protect the signals, then we have to do encryption/decryption a cell in each switch. That will bring a series adverse effects.
The first challenge in securing ATM network is how to find a cryptographic mechanism to match the high communication speed of a switch. Cryptography is used to provide confidentiality, authentication, and even integrity service for a security system. Unfortunately, most traditional cryptographic mechanisms operate within 10 Mbps when implemented in software or hundred Mbps when implemented in hardware. This speed is impossible to meet the speed of a switch, which normally will operate at hundreds of Mbps upto Gbps. Although [ HE92] had proposed an implementation of DES which can operate at Gbps, it takes a big time overhead to warm up when the session key changes. Due to key agility requirement we shall introduce, it's not a good solution to that problem. From here we can see why Phase I Security Specification hasn't addressed how to protect the cell header.
Another issue will rule out a lot of traditional cryptographic mechanisms. ATM cell payload is 48 bytes. Therefore any block cipher with block size more than 384 bits can not be applied to encrypt a cell. Even the block size of a cipher is smaller than 384 bits, the alignment of the cell and cipher block also affect the choice of a cryptographic algorithm. Phase I Security Specification will encounter this problem since the data confidentiality in user plane is on per cell basis.
An alternate for block ciphers is stream ciphers. However, this solution will suffer from the problem of resynchronization. If a cell is lost during the transmission, then when the receiver receives and decrypt the cell sequence, the data will look like garbage.
Even we can find a cryptographic mechanism which can meet the above requirements, high speed in ATM can introduce difficulties in key management. With such a high speed, ATM can transfer a high volume of data in a short time. Assume an ATM operates at a speed of 130Mbps. That means there can be 0.37M cells switching through a switch within one second. If we use DES cipher with block size of 64 bits, then about 2M DES cipher blocks will go through a switch per second. If the number of VCs running through this switch is not too big, then with such an amount data, an attacker can easily break the session key in a relatively short time. Notice that always assuming that the hacker can not access such a computing power is not true in a short future, or even now. To avoid this kind of attack, the system has to change the session key frequently. If we assume that one session key can not be used more than 100M cipher blocks, then the lifetime of a session key becomes as short as several hundred seconds. This will make a lot of traditional key exchange mechanism inadequate. Even we have a scheme which can successfully change the session key at this speed, that will introduce another problem. In traditional key exchange mechanism, session key will be encrypted by a permanent key. Frequently exchanging session key will give enough information to an attacker to break the permanent key in a relative short amount of time.
As suggested in Phase I Security Specification, security will be applied on a per VC basis. That is to say, an encryptor/decryptor will use different keys for different VC. One advantage of this method is to protect the confidentiality of other VC in case one VC has been compromised. Another advantage the life time of session key can be reasonable long since normally the traffic of one VC is not so high as the total traffic of the system(this assumption might not be true in the future if multimedia becomes popular over the ATM). With this method, the system can even provide different quality of security service to different VC, therefore to introduce the concept of QoS into the ATM security.
However, one difficulty to implement this scheme in ATM is that it requires the encryptor to have the ability to access a range of key data at a high speed[ TF95]. It also requires the encryptor can change the session key dynamically and apply to next cell very quickly. This requirement, called key agility, is non-trivial. As mentioned in [ HE92], some cryptographic algorithm require a long set up time when the encrypt key changes. Even worse, according to large number of potential VCs, looking up the key in big key table will introduce a time overhead which can be in the critical path therefore can be the bottleneck of the system.
Finally, according to the ATM's capacity to support multi-service traffic, how to charge the services and maintain a secure billing system are still unknown. And how to combine it with the electronic monetary systems is another interesting question.
ATM technology perhaps is the most complex networking technology we ever have. To secure such a complex system will be even more difficult than design it. And now people just begin to discuss some issues of ATM security. It will take times for us to figure out how to completely achieve our security objectives. Because the goal of ATM is to provide a unified networking platform and communication infrastructure, ATM security , as a part of this infrastructure, has to be flexible and compatible with other technology. That will introduce more difficulties to ATM security.
As we have discussed in this paper, we do achieve something in the past two years. As mentioned before, ATM Forum Security Working Group has come up with drafts for security specification and security framework. A lot of other security issues have been discussed in ATM Forum, as surveyed in this paper. The problem, although seems bigger and bigger, becomes more and more clear.
There are some products about ATM security available right now. Most of them are about encryption. For example, GTE introduces a product called InfoGuard 100 which provides secure delivery of ATM cells over local and wide area ATM networks. Another product of GTE is called FASTLANE encryptor which is claimed to provide high-speed, transparent, low-latency security services for multi-media applications across both local and wide area ATM networks. Secant Network Technologies offers a Key Agile Encryptor system called CellCase which can handle at least 35 calls per second. Network System claims that they have implemented a ATM firework system. Although these implementations are quite small compared to the big picture of the ATM security. It will provide some experience for us to implement security services in ATM network.
ATM Forum Constributions:
[SPEC97] Security Working Group, Phase I ATM Security Specification, ATM Forum BTD-SEC-01.03, July 1997
Proposing an ATM scurity infrastruture.
[FRWK97] Security Working Group, Security Framework for ATM Networks, ATM Forum BTD-SEC-FRWK-01.01, July 1997
Discussing the general functional requirements of ATM security system.
[KMN971] W Klasen, M. Munzert, and B. Nauer, Security Framework for ATM Networks, ATM FORUM/97-0068, Feb 1997
Proposing a security framework.
[KMN972] W Klasen, M. Munzert, and B. Nauer, Plane Specific interpretation of functional security requirement, ATM FORUM/97-0243, April 1997
Interpretation of security requirement for user plane.
[BNM97]G. Bogler, B. Nauer, and M. Munzert, Proposed work on management capabilities for ATM security, ATM FORUM/97-0067,Feb 1997
Discussing the need to include management capabilities in Phase I Security Specification.
[BMN97] G. Bogler, M. Munzert, and B. Nauer, Requirements and Protocol Independent MIB for the Management of the ATM Security Services, ATM FORUM/97-0237R1, July 1997
Proposing protocol for security management in control and user planes.
[HSK97] Kim Hebda, Linda Shields, and Chris Kubic, Selection and Negotiation of Multiple Algorithms to Support Security Services, ATM FORUM/97-0481, July 1997
Extending selection of security algorithm from two to more than two.
[SKH97] Linda Shields, Chris Kubic, and Kim Hebda, Control Panel Authentication, ATM FORUM/97-0502, July 1997
Proposing a method to use user plane data integrity to provide hop-by-hop authentication of signaling messages.
[PB972] Tony Przygienda, and Carter Bullard, Baseline Text for PNNI Peer Authentication and Cryptographic Data Integrity, ATM FORUM/97-0472, July 1997
Dicussing mechanism to secure PNNI messages.
[PB971] Tony Przygienda, and Carter Bullard, Mechanisms and Formats for PNNI Peer Authentication and Cryptographic Data Integrity, ATM FORUM/97-0252, April 1997
Original version of [PB972]
[KM97] W. Klasen, M. Munzert, Plane Specific Interpretation of Functional Security Requirements - Control Plane, ATM FORUM/ 97-0529, July 1997
Interpretating the security requirements proposed in ATM scurity framework in contral plane.
[BW96] G. Bautz, K. Wrona, Security requirements for WATM Systems, ATM FORUM/96-1216, Oct 1996
Identifying the basic security reuqirement for wireless ATM.
[BW97] G. Bautz, K. Wrona, Proposal to include Security for Wireless ATM into the phase 2 working scope of the SEC WG, ATM FORUM/97-0532, July 1997
Discussing the need to include security for wireless ATM into ATM security scope.
[CF97] C. Clanton, L. D. Finkelstein, Proposed Definition of the Wireless ATM Security Problem, ATM FORUM/97-0594
Discussion about the general security problem about wireless ATM.
[Bullard97] Carter Bullard, ATM Forum Security Agent Specification, ATM Forum/97-0408, April 1997
Introducing the concept of security agents.
[MH95]]M. Peyravian and E. V. Herreweghen,ATM Scope & Requirement, ATM FORUM/95-0579
Discussing basic security requrements for ATM security.
[TF95] Richard Taylor, Greg Findlow, Asynchronous Transfer Mode: Security Issues, Proc. Aus tralian Telecommunication Networks and Applications Conference;pp. 161-166, 5-7 Dec. 1995; pp. 161-166
Discussing basic threats and countermeasures of ATM security. A security architecture is also discussed.
[ALLES95] Anthony Alles, ATM Internetworking, presented at Engineering InterOp, Las Vegas, March 1995
Has mentioned the security problems when ATM is connected by internet.
[KB96] J. Kimmins and B. Booth: "Security for ATM networks"; Computer Security Journal; XII(1):21-29; 1996
Discussing relevant aspects of ATM security.
[Deng95] R. Deng et al: "Securing Data Transfer in Asynchronous Transfer Mode Networks"; Proceedings of GLOBECOM'95, Singapore, November 13-17, 1995, pp. 1198-1202
Dicussing security requirements and security architecture for ATM networks.
[Chuang96] Shaw-Cheng Chuang: "Securing {ATM} Networks",3rd {ACM} Conference on Computer and Communications Security, New Delhi, India, 1996, pp.19-30
Discussing challenges, secutiy mechanism placement and security requirements of ATM networks.
[SHBW95] Daniel Stevenson, Nathan Hillery, Greg Byrd and Dan Winkelstein, Design of a Key Agile Cryptographic System for OC-12c Rate ATM, Internet Society Symposium on Network and Distributed Systems Security,Feb 1995
[SHB95]D. Stevenson and N. Hillery and G. Byrd, Secure communications in {ATM} networks Communications of the ACM, Volume 38, No 2, pp 45--52, Feb, 1995
Discussing issues like security threats, cell encryption and securing call setup in ATM network.
[Sem94] W. Semancik et al: "Cell level encryption for ATM networks and some results from initial testing"; Proc. DoD Fiber Optics `94 Conf.; Armed Forces Commun. and Elect. Assn.; Mar 22-24; 1994
[Hanson95] L. Hanson, "The Impact of ATM on Security in Data Network", Proc. of Compsec International 1995, Conf. 12, pp 318-324
[Chuang95] S.C Chuang, "A Flexible and Secure Multicast Architecture for ATM Networks, Global Telecomunication Coference, Nov. 1995, pp. 701-707
[LPR97] Maryline Laurent, Olivier Paul, Pierre Rolin," Securing communications over ATM networks", IFIPSEC'97, Copenhagen, Denmark, May 1997
[[Lau96] Maryline Laurent, "Security Flows Analysis of the ATM Emulated LAN Architecture" , IFIP,Conference on Communications and Multimedia Security, Essen, Germany, September 1996
[HE92] H. Eberle, A High Speed DES Implementation for Network Applications, Advances in Cryptology-CRYPTO 92, Berlin:Spring-Verlay, pp. 527-545,1993
[BACON] M. Bacon, Security: a question of confidence, Telecommunications (int. ed.) (USA) Vol. 23, No. 11, pp 51-52, Nov. 1989
[CLS89]. W. Caelli, D. Longley and M. Shain, Information Security for Managers, Macmillan U.K., Stockton Press Canada, 1989
[MP93] M. Purser, Secure Data Networking, Artech House USA, 1993
[SP89]. J. Seberry and J. Pieprzyk, Cryptography: An Introduction to Computer Security, Prentice Hall, 1989
[DL95] H. Dutton and P. Lenhard, "Asnchronous Transfer Mode (ATM) Technical Overview", 2nd Ed., Prentice Hall, 1995
[CL95] T. M. Chen, and S. S. Liu, "ATM Switching Systems", Artech House, INC., 1995
Last Modified 8/14/1997.