Ria Das, ria.das@wustl.edu (A paper written under the guidance of Prof. Raj Jain)
|
Ria Das, ria.das@wustl.edu (A paper written under the guidance of Prof. Raj Jain) |
Download |
Internet of Things (IoT) refers to the next phase of information revolution whose context involves billions of smart devices and sensors interconnected to facilitate speedy information and data exchange under soft real time constraints. IoT extends the ‘anywhere, anyhow, anytime‘ computing and networking paradigm to ‘anything, anyone and any service‘. In this paper, a security scheme in IoT is analyzed where a fused approach of cryptography and steganography have been adopted. Two different steganographic schemes; Variable Least Significant Bit Substitution (VLSBS) and Most Significant Bit- Least Significant Bit (MSB-LSB) Substitution are analyzed using an experimental 24 X 3 design (48 experiments). Further an extensive literature survey is conducted in the steganography domain, to get an idea about popular steganographic metrics widely employed nowadays. Some of these metrics such as Peak Signal to Noise Ratio (PSNR), Mean Square Error (MSE) , Normalized Cross Correlation (NCC), Normalized Absolute Error (NAE), Average Difference (AD), Maximum Difference (MD), Structural Content (SC) etc have been analyzed for the aforesaid steganographic schemes for the purpose of comparative performance analysis. Further, it has been verified that the number of cover image pixels required for data embedding as well as number of altered cover image pixels is less in case of MSB-LSB scheme that implies its better performance as compared to its VLSBS counterpart.
Keywords. Internet of Things (IoT), Steganography, Cryptography, Variable Least Significant Bit Substitution (VLSBS), Most Significant Bit - Least Significant Bit (MSB-LSB) Substitution, Data Encryption Standard (DES), Peak Signal to Noise Ratio (PSNR), Mean Squared Error (MSE), Normalized Cross Correlation (NCC), Normalized Absolute Error (NAE), Average Difference (AD), Maximum Difference (MD), Structural Content (SC), Structural Similarity Index (SSIM).
2.1. Image Steganography Combined with DES Encryption Pre-processing
2.2. Comparative Analysis of Steganographic Algorithms Within Compressed Video Domain
2.4. A Cost Effective Approach for Securing Medical X-ray Images using Chebyshev Map
2.5. Local Binary Pattern Operator based Steganography in Wavelet Domain
2.6. Performance Analysis of Digital Image Steganographic Algorithm
2.7. Steganography based information security with high embedding capacity
2.8. 2L-DWTS – Steganography technique based on second level DWT
2.9. Secret Data Transmission using Vital Image Steganography over Transposition Cipher
2.10. Performance Evaluation Parameters of Image Steganography Techniques
2.12. Objective Quality Metrics in Correlation with Subjective Quality Metrics for Steganography
2.13. Enhanced Data Concealing Technique to Secure Medical Image in Telemedicine Applications
2.14. Stochastic Local Search Combined with LSB Technique for Image Steganography
The Internet has transformed into Internet of Things (IoT) propelled by the ever
increasing and spectacular advancements conducted in the domain of mobile
communications and wireless technologies. IoT refers to the next phase of
information revolution whose context involves billions of smart devices and sensors
interconnected to facilitate speedy information and data exchange under real time
constraints. The phrase 'Things' refer to the inseperable mixture of
hardware,software, data and services. IoT extends the 'anywhere, anyhow, anytime'
computing and networking paradigm to 'anything, anyone and any service'.
However, since IoT typically involves multitude of constrained devices i.e sensors
with limited computing power, battery life, memory, storage constraints, it is highly
vulnerable to attacks. Thus ensuring data security during information exchange phase
is of paramount importance in IoT.
In this paper, two proposed security schemes in IoT are analyzed employing a
merged approach of Cryptography and Steganography schemes mentioned in
papers [Das17-Das16]. The goal here is to evaluate and examine the performance of the proposed security
steganograhic schemes using various popular steganographic and performance
metrics.
Cryptography refers to the science of attaining security by encrypting messages to
make them non-readable. The process of converting from the plaintext (original data)
to ciphertext (coded data) is known as encryption while the reverse process is termed as
decryption. If the same key is utilized for both encryption and decryption then the
cryptographic model is termed a Symmetric Cryptography model else Asymmetric
Cryptography. In IoT lightweight Cryptography is desirable since IoT devices are
constrained devices and lightweight schemes provide high efficiency for end-to- end
communications as well as can be applied on low resource devices.
Steganography, on the other hand, refers to 'covered or hidden writing'. The goal of
this scheme is to hide the very existence of the message/data in a cover medium.
Modern steganographic schemes employ various cover mediums like the audio,
image,video, network/protocols etc to embed data securely and then transmit it over
the network. Applications of Steganography exist primarily in secret communications,
feature tagging, copyright protection etc.
Eavesdropping is a very typical attack which is highly likely in IoT environment. One
such scenario has been depicted in the Fig.1 below. It displays the data flow in the
system under investigation. Firstly, the sensor captures the data which is transferred to
an Authentication Server/Home Server for authentication purpose. Next, the data is
migrated to the Clouds for further computation and analysis as per the requirements of
deployed IoT applications. As shown the transferred data can be subjected to an
eavesdropping attack. To address the aforesaid issue, an interesting model has been
undertaken. A combined approach of Cryptography and Steganography scheme can
be adopted to ensure data confidentiality and integrity. The implementation of the
adopted scheme is next discussed briefly.
![Fig.1. IoT Scenario [Das16]](./fig1.png)
![Fig.2. Proposed Security model in IoT adopting VLSBS scheme [Das17]](./fig2.png)
![Fig.3. Proposed Security model in IoT adopting the MSB-LSB scheme [Das16]](./fig3.png)
In this paper, performance analysis is conducted for all the above implemented
security schemes along with the computation of some popular steganographic
performance metrics. An extensive literature survey is conducted in this domain the
details of which are presented in the literature review section of this paper.
The structure for this paper is organized as follows. Section 2 highlights the
literature survey conducted in the domain of Steganography highlighting some of the
popular performance metrics. Section 3 puts forth overview of the proposed
steganographic schemes: SLSBS, VLSBS and MSB-LSB schemes as adopted in
papers [Das17-Das16]. Section 4 analyzes the computed performance metrics along with the
experimental computations. Finally section 5 discusses the concluding section of this paper.
Already several researchers worldwide have worked in the domain of Cryptography
and Steganography and thus have adopted various metrics for analyzing the
performance of their proposed methodologies and schemes. In this section briefly,
some of such existent works and the analyzed metrics have been put forth.
Researcher B. Lakshmi Sirisha et.al. have proposed a high embedding capacity for spatial domain image steganography in this work. By employing the (t, n) threshold secret sharing scheme, here two secret images are embedded in a cover image of same size with relatively high quality. In this approach, the secret image is communicated among n participants. Additionally, any t (or more) out of n authorized participants can only recover the secret image whereas less than t participants however cannot reconstruct the same.
The performance metrics used in this work includes the follows: i) Peak Signal to Noise Ratio (PSNR) ii) Mean Squared Error (MSE) iii) Structural Similarity Index (SSIM) iv) Average Difference (AD) v) Normalized Cross-Correlation (NCC) vi) Normalized Absolute Error (NAE) that have been already discussed in the previous papers.
Researchers Punam Bedi et.al. have undertaken a steganographic technique here that is primarily based on Discrete Wavelet Transform (DWT) scheme. In this work a novel steganography technique 2L-DWTS is proposed, which applies discrete wavelet transform twice on the cover image and embeds the secret data or message in second level high frequency components. To retrieve the stego image, inverse DWT is employed on these components. Veiling the data in one of these high frequency components is not reflected since data spreads evenly across the stego image. Applying DWT twice appends an additional security layer specifically generating sixteen components which facilitates hiding four times stronger to susceptibility.
The performance metrics which have been analyzed in this work consists of the follows; i) Peak Signal to Noise Ratio (PSNR) ii) Mean Squared Error (MSE) iii) Structural Content (SC) iv) Normalized Cross-Correlation (NCC) v) Normalized Absolute Error (NAE) and vi) Image Infidelity (IF). Most of these have been already discussed above.
Image Infidelity (IF) is computed when an accurate match is sought between the stego and cover image without having any visible distortion or loss of information.
Researchers Mamta Jain et.al. in this work have performed secret data transmission employing vital image steganography scheme over transposition cipher. In this work, two varieties of security mechanism have been considered; cryptography and steganography. First, encryption is performed adopting Vernam cipher (One-Time Pad) transposition technique scheme. Next, cipher text is transformed into bytes and each byte divided into bit pairs and the decimal values are assigned to each pairs, which is termed as the master variable (Value of master variable varies between 0 to 3). Depending upon the master patchy value, the cipher text in the career image is added at Least Significant Bit (LSB) 6th and 7th bit location or 7th and 8th bit location or 7th and 6th or 8th and 7th bit locations. Eventually the cipher texts are retrieved from the said locations followed by the decryption process using the Vernam cipher (One-Time Pad) transposition algorithm.
The performance metrics that have been considered here are i) Peak Signal to Noise Ratio (PSNR) and ii) Mean Squared Error (MSE) which have been already described above.
Researchers Anita Pradhan et.al. have in this work highlighted some of the performance evaluation parameters of Image Steganography schemes. The performance of a steganographic technique can be rated by three parameters; i) hiding capacity, ii) distortion measure and iii) security. The hiding capacity refers to the maximum quantity of information that can be embedded in an image which is also represented as the number of bits per pixel. The distortion is measured by using various metrics like i) Peak Signal to Noise Ratio (PSNR) ii) Mean Squared Error (MSE) iii) Structural Similarity Index (SSIM), Correlation etc all of which have been already highlighted in the previous works.
Researchers Mansi S. Subhedar et.al. in this work have presented a novel idea to hide secret data in contourlet domain. Here, the cover selection criteria is based on contrast measurement. Using contrast measurement, suitable cover is chosen from standard test image database and then embedding is carried out in contourlet sub bands of cover image.
The performance metrics that have been analyzed here includes the follows; i) Peak Signal to Noise Ratio (PSNR) ii) Mean Squared Error (MSE) iii) Structural Similarity Index (SSIM) all of which have been discussed earlier.
Researchers Raniyah Wazirali et.al. have conducted a comparative study between objective quality metrics with subjective quality metrics in this work. Most of the ongoing studies employ the Peak Signal to Noise Ratio (PSNR) as a metric for imperceptibility evaluation, although it furnishes less accurate results as compared to the Human Visual System (HVS) evaluation. This paper provides a review of the existent evaluation metrics that are used to assess the quality of adopted steganographic scheme.
The performance metrics which have been adopted here includes; i) Peak Signal to Noise Ratio (PSNR) ii) Mean Squared Error (MSE) and iii) Structural Similarity Index (SSIM) all of which has been explicitly described earlier.
Reserachers G. Vallathan et.al. have performed an enhanced data hiding scheme to secure medical image transference in telemedicine applications. In this paper, both encryption and steganography technique have been employed to improve the security of both patient's privacy information as well as the medical image. The host medical image undergoes Contourlet Transform to provide the innate geometrical structures of an image like curves instead of points and it offers the directionality and anisotropy property. Next, the patient privacy information is embedded over the high frequency components of a transformed image using LSB embedding algorithm. Finally the data concealed image is encrypted using LBG (Linde Buzo Gray) algorithm to ensure security.
The performance metrics which have been analyzed here comprises the follows; i) Peak Signal to Noise Ratio (PSNR) ii) Mean Squared Error (MSE) and iii) Structural Similarity Index (SSIM) all of which have been explicitly discussed above.
Researchers Dalila Boughaci et.al. have proposed a novel steganographic methodology to hide a message in the image. The proposed technique adopts an integrated approach of Stochastic Local Search meta-heuristic (SLS) with the least significant bits method (LSB).The LSB approach was improved by combining it with the SLS technique. Here the researchers have adopted 3 methods LSB (Least Significant Bit), LSB + LS (local search) and LSB+ SLS (stochastic local search) and evaluated all on some series of JPEG images.
The performance metrics which have been analyzed here comprises the follows; i) Peak Signal to Noise Ratio (PSNR) ii) Mean Squared Error (MSE) and iii) the Encoding Time all proposed schemes.
Thus, in this section, a detailed literature survey has been furnished that gives idea about some of the widely employed steganographic performance metrics for experimental evaluation purpose in the domain of Steganography. In the next section 3 an overview of the proposed and adopted Steganographic schemes in papers [Das17-Das16] have been put forth.
This section outlines a detailed discussion of the proposed steganography algorithms i.e Simple LSB (SLSBS), Variable LSB (VLSBS) and MSB-LSB schemes undertaken in the research work from papers [Das17-Das16].For implementing steganographic schemes, the cover image is taken in any format (.jpeg, .png etc) and it is converted into bitmap (.bmp) format since that offers lossless uncompressed image version. The following section outlines the proposed steganography schemes briefly.
The Simple Least Significant Bit Substitution (SLSBS) method is very familiar and one of the preliminary steganography schemes that performs replacement of the least significant bit of each cover image pixel with respect to the embedding message bit. The simple condition of replacement is, if the message bit is 1 and the corresponding LSB of the cover image pixel where the message bit is to be embedded is 0 or the message bit is 0 and corresponding LSB of the cover image pixel is 1 i.e. whenever contradiction happens then only substitution is performed. Else, the LSB of cover image pixel remains unaltered. So, each cover image pixel suffers from 50% probability of being flipped. This scheme is popular because i) it is very simple ii) offers lower computational complexity in comparison to conventional standardized cryptographic schemes and iii) its ability to transfer data securely.
To incorporate randomness & variation, in the Variable Least Significant Bit Substitution (VLSBS) scheme, a hashing algorithm is used that randomly maps pixel values of cover image to different targeted hash mapped pixel values each time where the message/data bit gets embedded. Thus that offers better security against confidentiality attacks & replay attacks, if launched by intruders as compared to SLSBS scheme.
Using the SLSBS scheme the message bits were being embedded in the cover image pixels sequentially (from 55th pixel onwards since first 54 pixels contain essential information about image header and cannot be modified). But in the VLSBS scheme a hash algorithm is used that randomly maps the cover image pixels to discrete values, unevenly where the actual embedding of message bits is furnished. This incorporates randomness while embedding data bits and thus offers better security against attacks as launched by intruders or adversaries.
Single bit LSB substitution is a renowned algorithm and it can only substitute a single bit of data in each carrier pixel (in this case carrier is image); there is no scope of embedding more data bits inside the cover medium. So, this devised scheme employs an algorithm to use MSB and LSB positions of cover image pixel to substitute, which can embed maximum 2 data bits. Thus the advantage lies in the fact that the image quality is not sacrificed much and it is identical to simple LSB substitution algorithm (degree of substitution is 1), but maximum 2 message bits can be embedded here, whereas Simple LSB could embed only 1 message bit.
Fig.4 and Fig.5 below depicts a sample input cover image and corresponding stego obtained by applying the aforesaid schemes for both small and large sample image sizes.
Fig.4 Original Image and Stego Image (for small cover image size)
Fig.5 Original Image and Stego Image (for large cover image size)
Thus, in this section, the various adopted schemes of Steganography as highlighted in the work [Das17-Das16] has been furnished in detail. The following section 4 discusses the experimental design overview and highlights some of the steganographic performance metrics undertaken for performance analysis of the aforementioned steganographic schemes.
In this section a brief outline of the undertaken experimental design and performance metrics have been highlighted which have been employed to estimate the performance of the proposed steganographic schemes; VLSBS and MSB-LSB as depicted in papers [Das17-Das16].
There are four primary factors which have been considered in experimental design for performance analysis purpose that includes i) the type of proposed steganographic approach (VLSBS and MSB_LSB schemes), ii) processor type (Intel Core i5 and Intel Pentium CPU N3530), iii) cover image size 462 KB (Lenna.png) and 1.27 MB (Peppers.jpg) and iv) data sizes (small having 3 characters and large having 14 characters) are also considered in some situations for analysis.
For the sake of experimental purpose, first both the algorithms (VLSBS and MSB-LSB) are simulated in MATLAB environment. Varying data inputs are given (all are character inputs: USA (3 characters: 24 bits), UNITED KINGDOM (14 characters: 112 bits) sizes. Following is the concise list of performance metrics that have been chosen for analysis purpose:
A 24 X 3 (2k X r) factorial design = 48 experiments is considered taking into account the program execution time three times (replication r=3) adopting two different type of proposed steganographic approaches (VLSBS and MSB_LSB schemes), two different data sizes (small: 3 characters and large: 14 characters), two different processor types (Intel core i5 and Intel Pentium CPU N3530) and two different image sizes (Lenna: 462 KB and Peppers: 1.27 MB). The impact of the various factors is computed using the 24 X 3 factorial designs where each factors have two levels. Next the visual tests are conducted for further analysis purpose.
Additionally the Ranking method is undertaken to check the impact of all enlisted factors: image sizes, data sizes, type of processor, type of proposed steganographic approach at a glance.
Further corresponding to each proposed steganographic approaches (i.e SLSBS, VLSBS and MSB-LSB schemes) some popular metrics such as (Mean Squared Error) MSE, (Peak Signal to Noise Ratio) PSNR, (Normalized Cross-Correlation) NCC, (Average Difference) AD, (Structural Content) SC, (Maximum Difference) MD and (Normalized Absolute Error) NAE, number of cover image pixels altered and required for embedding are also computed to compare the performance among the proposed steganographic approaches as suggested from the literature survey metrics has been highlighted in section 2 of this paper.
In this section, the brief overview of factors and experimental design has been highlighted along with the enlisted performance steganographic metrics that have been analyzed. The following section details the performance computations and analysis done as per the aforesaid enlisted metrics.
In this section the experimental data sets of 24 X 3 design and the computation analysis are discussed below:
The following Table.I enlists the undertaken factors and their corresponding levels.
Table.I. Factor Levels
The following Table.II depicts the factor level combinations and the mean program execution time as follows:
Here we have four main effects (A, B, C and D), six (AB, AD, BC, BD, AC, CD) two factor interactions, four (ABC, ABD, ACD, BCD) three factor interactions and one (ABCD) four factor interaction in this 24 X 3 design.
From the above highlighted design applying the Ranking method it can be concluded that best factor combination levels corresponding to minimum program execution time is when B=C=D= -1. It implies that on Intel core i5 processor with small cover image and data sizes, the program execution time is the least; thus the best.
After the computations it can be concluded that in decreasing order factors C, D, B, A, AC, CD interactions are important as compared to the other interactions (AB, AD, BC, BD, AD, ABC, ABD, ACD, BCD, ABCD that are negligible).
Thus it can be concluded that the performance of steganographic schemes largely depends on the cover image size, data/message length size followed by the interaction between type of proposed steganographic scheme and the cover image size. Next it can be inferred that the type of processor and adopted steganographic scheme has little effect on the performance of the steganographic algorithms.
Table.II. Factor Level Combinations
Thus it can be deduced that the performance of steganographic schemes largely depends on the cover image size, data/message length size followed by the interaction between type of proposed steganographic scheme and the cover image size. Next, it can be summarized that the type of processor and adopted steganographic scheme has little effect on the performance of the steganographic algorithms. The % variation unexplained and attributed to errors is 0.80% while the rest 99.2 % is explained by this regression model. Thus this model can be termed as a good model.
So, in the following Table.III only the important factor contributions are calculated ignoring the rest.
Table.III. Confidence Intervals and % Variation explained by the enlisted Factors
Thus all the effects are significant since none of the above factors include 0 in its Confidence Intervals.
From the Quantile Quantile plot shown below in Fig.6, it can be concluded that the graph appears to be approximately linear and thus the data passes the normality test. Further the plot of residuals versus the predicted response as shown in Fig.7 clearly shows that the spread of residuals/errors is constant and the errors are randomly distributed.
Thus in this section the experimental evaluations, designs, factor level combinations and outcomes have been discussed in detail. The next subsection highlights some of the adopted well known steganographic metrics which have been analyzed for the proposed steganographic schemes as highlighted in section 4 of this paper.
As per the highlighted literature review conducted in the Steganography domain presented in section 2 of this paper, some of the well-known steganographic metrics (mathematical expressions of which are presented in Table IV below) have been computed here to compare the performance of proposed schemes SLSBS, VLSBS and MSB-LSB approaches for the purpose of further analysis. As a result, a varying data set to simulate the programs (Inputs: USA- 3 characters, INDIA - 5 characters, BOLIVIA -7 characters, AUSTRALIA - 9 characters and UNITED KINGDOM - 14 characters) have been considered and accordingly the following metrics have been computed that is enlisted in the Table.V and Table. VI below.
Further a comparative study of both the VLSBS and MSB-LSB schemes is facilitated here. The number of cover image pixels required for embedding data bits as well as the number of cover image pixels altered in MSB-LSB scheme is lower as compared to its VLSBS counterpart. Thus MSB-LSB scheme performs better than VLSBS scheme. The plots of relevant graphs have been shown in Fig.8 and Fig.9 below. Fig.10 shows the histogram of the original cover image and stego image that shows that there is not much alteration, hardly visible between original cover and stego image.
Table.IV. Mathematical Expressions of Image Steganographic Metrics
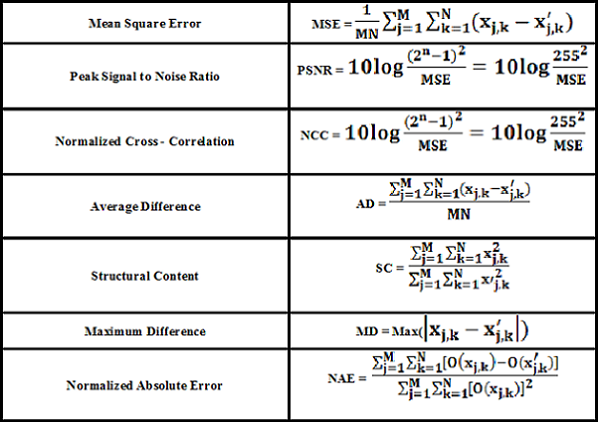
Table.V. Steganographic Metric Computations( Image Lenna )
Table.VI. Steganographic Metric Computations( Image Pepper )
From the Table. V and Table. VI, it is clear that the Peak Signal to Noise Ratio (PNSR) value range between 91.5244 dB to 113.3932dB (high value implies good performance). Mean Squared Error (MSE) value is very low for all experiments. The Normalized Cross Correlation (NCC), Structural Content (SC) is 1 for all experiment which implies that there is high similarity between cover image and generated stego image. Average Difference (AD) between two selected pixel values of cover and stego image is very low. Maximum Difference (MD) is used to measure the cover and stego and the compressed quality of stego image, whose value is low means high quality result. Normalized Absolute Error (NAE) is the statistical difference between the cover and stego image. The small value indicates high quality.
In this paper, performance analysis is done to compare performances of two modified LSB Steganography algorithms namely: VLSBS and MSB-LSB which have been put forth as a security model in papers [Das17-Das16]. An extensive literature survey has been conducted in the Steganographic domain, so as to get the idea of well-known steganographic metrics that are widely employed nowadays to compare the performances of aforementioned steganographic schemes. The primary factors that affect the performance of steganographic algorithms have been enlisted. Further a 24X 3 experimental design (48 experiments) is undertaken to quantify the effects of the enlisted factors.
After computation it has been observed that the program execution time of steganographic schemes largely depends upon the cover image size, data/message length size followed by the interaction between type of proposed steganographic scheme and the cover image size. Also from the computations of various steganographic metrics like (Mean Squared Error) MSE, (Peak Signal to Noise Ratio) PSNR, (Normalized Cross-Correlation) NCC, (Average Difference) AD, (Structural Content) SC, (Maximum Difference) MD and (Normalized Absolute Error) NAE, number of cover image pixels altered and required for embedding it can be concluded that the performance of proposed MSB-LSB scheme is better as compared to its VLSBS or SLSBS counterpart.
[1] AD: Average Difference
[2] BER: Bit Error Rate
[3] CR: Compression Ratio
[4] DCT : Discrete Cosine Transformation
[5] DES : Data Encryption Standard
[6] DFT : Discrete Fourier Transformation
[7] DWT: Discrete Wavelet Transformation
[8] EPVD: Enhanced version of Pixel Value Difference
[9] IoT : Internet of Things
[10] IF: Image Infidelity
[11] IWT: Integer Wavelet Transformation
[12] LBG : Linde Buzo Gray
[13] MD : Maximum Difference
[14] MD5: Message Digest 5
[15] MSB-LSB : Most Significant Bit- Least Significant Bit
[16] MSE : Mean Squared Error
[17] NAE: Normalized Absolute Error
[18] NCC : Normalized Cross Correlation
[19] PRD: Percentage Residual Difference
[20] PSNR : Peak Signal to Noise Ratio
[21] SC: Structural Content
[22] SSIM: Structural Similarity Index
[23] SLS: Stochastic Local Search
[24] VLSBS : Variable Least Significant Bit Substitution