| Yoon Jae Kim, yj1dreamer AT gmail.com (A project report written under the guidance of Prof. Raj Jain) |
Download |
Service Oriented Architecture (SOA) is a design pattern which is composed of loosely coupled, discoverable, reusable, inter-operable platform agnostic services in which each of these services follow a well defined standard. Each of these services can be bound or unbound at any time and as needed. [Jamil08]
However, as defined, SOA has a loosely-coupled feature, which makes SOA open to the challenges of security. It means that SOA must meet several requirements. The main requirements are as follows[Candolin07]: service discovery, service authentication, user authentication, access control, confidentiality, integrity, availability, and privacy. To ensure security in a loosely-coupled SOA environment, the open standards communities that created Web services developed a number of security standards for Web services which is one of the most active and widely adopted implementation of SOA. Figure 1 depicts a notional reference model for Web services security standards. This reference model maps the different standards to the different functional layers of a typical Web service implementation.
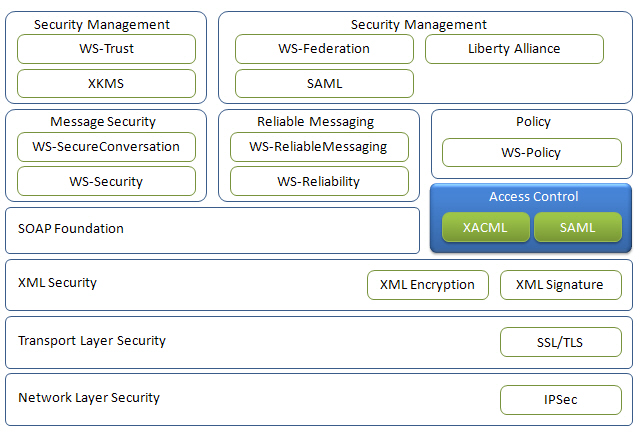
As described above, in the Web Services Security Stack the Security Assertion Markup Language (SAML) and the eXtensible Access Control Markup Language (XACML) are the standard for access control which means that when the service is requested by a user the service must enforce the specified security policy related to access control. We focus on access control in the Web Services security and represent what SAML and XACML are, how they work and where they are able to be applied together.
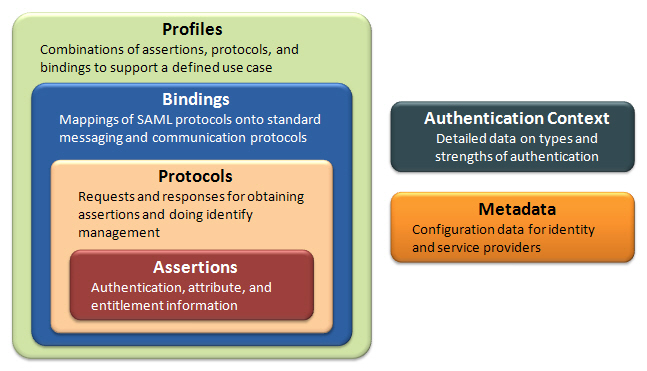
SAML, created by the Security Services Technical Committee of the Organization for the Advancement of Structured Information Standards (OASIS), is a an XML-based framework for communicating user authentication, entitlement, and attribute information. As its name suggests, SAML allows business entities to make assertions regarding the identity, attributes, and entitlements of a subject (an entity that is often a human user) to other entities, such as a partner company or another enterprise application. [Madsen05] SAML is a flexible and extensible protocol designed to be used - and customized if necessary - by other standards.
Web Single Sign-On
In web SSO, a user authenticates to one web site and then, without additional authentication, is able to access some personalized
or customized resources at another site. SAML enables web SSO through the communication of an authentication assertion from the
first site to the second which, if confident of the origin of the assertion, can choose to log in the user as if they had
authenticated directly. A principal authenticates at the identity provider and is subsequently appropriately recognized
(and given corresponding access/service) at the service provider.[Google]
For example, Google made SAML Single Sign-On (SSO) Service for Google Apps. And Google Apps provides a SAML-based Single Sign-On (SSO) service that offers partner companies with full control over the authorization and authentication of hosted user accounts that can access web-based applications like Gmail or Google Calendar. As the service provider Google offers services as Gmail and Start Pages and partner companies control account information as identity provider.
Attribute-Based Authorization
Similar to the Web SSO scenario, the attribute-based authorization model has one web site communicating identity information about
a subject to another web site in support of some transaction.
However, the identity information may be some characteristic of the subject (such as a person's role in a B2B scenario) rather than, or in addition to, information about when and how the person was authenticated. The attribute-based authorization model is important when the individual's particular identity is either not important, should not be shared for privacy reasons, or is insufficient on its own.
Securing Web Services
SAML assertions can be used within SOAP messages in order to convey security and identity information between actors in web
service interactions. The SAML Token Profile produced by the OASIS Web Services Security (WSS) TC specifies how SAML assertions
should be used for this purpose with the WS-Security framework. The Liberty Alliance's Identity Web Service Framework (ID-WSF)
builds on these specifications to use SAML assertions for enabling secure and privacy-respecting access to web services.
WS-Trust, one component of the private WS-* framework initiative, proposes protocols for the exchange and validation of security tokens used as described within WS-Security. SAML assertions are one such supported security token format.
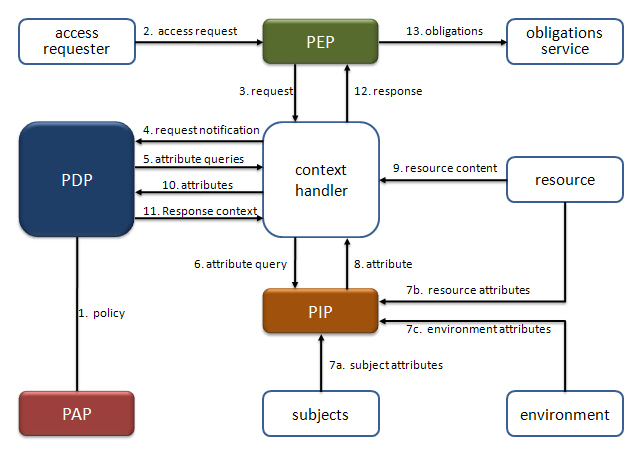
Figure 3 illustrates these actors and information flow. As can be seen in the figure, the PAP writes Polices and PolicySets and makes them available to the PDP. These Policies or PolicySets shows the complete policy for a particular target. The PEP is the component where the request is received when access requester wants to take some action on a resource and make the request. In this part, the attributes in the request may be in the format of the application environment (e.g., SAML, etc.). The PEP sends the request to the Context Handler. Context Handler maps the request and attributes to the XACML Request context and sends the request to the PDP. While evaluating the request, the PDP needs some attributes and sends the attribute queries to the Context Handler. The Context Handler collects these attributes by the help of the PIP from the resources, subjects, and the environment. After evaluation, the PDP sends the XACML Response to the Context Handler and the Context Handler translates the Response context to the native response format of the application environment and sends it to PEP. The PEP fulfills the obligations if they exist and applies the authorization decision that PDP concludes.[Periorellis07]
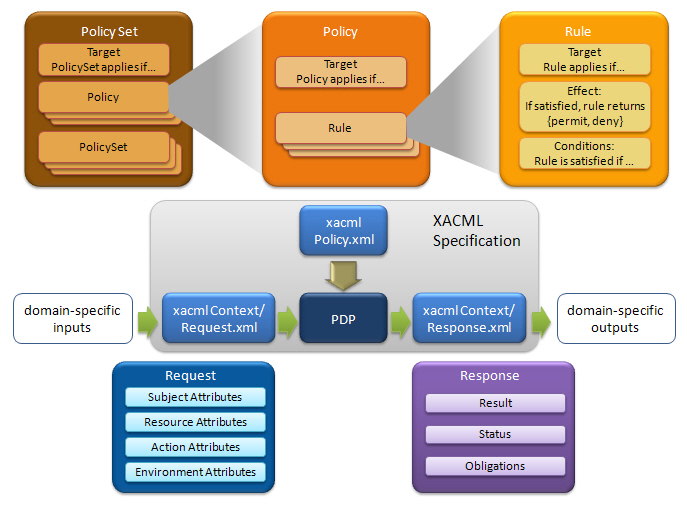
A Request element contains four components as Subject, Resource, Action, and Environment. One request element has only one collection of resource and action attributes, and at most one collection of environment attributes. But there may be multiple collections of subject attributes. Subject attribute contains subject's details such as name, e-mail, role and so on. Resource attribute details the resource for which access is requested and action attribute specifies the requested action to be performed on resource such as read or wire. Also, Environment attribute is optional and contains attributes of environment.
A Response element represents the authorization decision information made by PDP. It contains one or more Result attributes. Each result includes a Decision such as Permit, Deny, NotApplicable, or Indeterminate, some Status information which gives the errors occurred and their descriptions while evaluating the request and optionally one or more Obligations which specifies tasks in the PolicySet and Policy elements in the policy description which should be performed before granting or denying access.
A Rule element defines the target elements to which the rule is applied and details conditions to apply the rule and has three components such as target, effect, and condition. A target element specifies the resources, subjects, actions and the environment to which the rule is applied. A condition element shows the conditions to apply the rule and a effect is the consequence of the rule as either permit or deny.
A policy is the set of rules which are combined with some algorithms. These algorithms are called Rule-combining algorithms. For instance "Permit Override" algorithm allows the policy to evaluate to "Permit" if any rule in the policy evaluates to "Permit". A policy also contains target elements which shows the subjects, resources, actions, environment that policy is applied.
A PolicySet consists of Policies and PolicySets combined with policy-combined algorithm. It has also target like a Policy.
The XACML context shows how flexible and suitable the XACML is for various application. This feature makes it possible that XACML is applied to access control system with SAML. Section 4 shows the more detailed.
SAML is one standard suitable for providing the assertion and protocol mechanisms and specifies schemas for carrying the security and authorization related information and have the bindings to basic transportation mechanisms. Therefore, OASIS publishes a SAML profile for the XACML (OASIS, 2005)[Anderson05] to carry the XACML messages between the XACML actors. This profile defines the usage of SAML 2.0 to protect, store, transport, request and respond with XACML instances and other information. It contains largely four categories.
First, this profile specifies how to use SAML Attributes in an XACML system. This category contains three standard SAML elements such as SAML Attribute, SAML AttributeStatement and SAML Assertion, two standard SAML protocol such as SAML AttributeQuery and SAML Response, and one new SAML extension element, XACMLAssertion. In an XACML system, SAML Attribute may be used to store and to transmit attribute values and must be transformed into an XACML Attribute before used in an XACML Request Context. Also SAML AttributeStatement may be used to hold SAML Attribute instances. A SAML Assertion may be used to hold SAML AttributeStatement instances in an XACML system, either in an Attribute Repository or in a SAML Response to a SAML AttributeQuery. To transform a SAML Attribute into an XACML Attribute the SAML Assertion includes information that is required and a SAML Assertion or an XACMLAssertion instance contains a SAML Attribute. An XACMLAssertion is an alternative to the SAML Assertion and allows inclusion of XACML Statement instances and inclusion of other XACMLAssertion instance as advice. An XACML PDP or PEP use SAML AttributeQuery to request SAML Attribute instances from an Attribute Authority for use in an XACML Request Context and in response to it SAML Response shall be used to return SAML Attribute instances.
Second, this profile represent the use of SAML for use in requesting, responding with, storing, and transmitting authorization decisions in an XACML system. This category contains XACMLAuthzDecisionStatement, XACMLAssertion, XACMLAuthzDecisionQuery, and XACMLResponse. In this profile, XACMLAuthzDecisionStatement and XACMLAssertion are new SAML extension elements and the others are new SAML extension protocol elements. In an XACML system, XACMLAuthzDecisionSatement may be used to contain XACML authorization decisions for storage or transmission and XACMLAssertion may be used to contain XACMLAuthzDecisionStatement instances for storage or transmission. Also a PEP may use XACMLAuthzDecisionQuery to request an authorization decision from an XACML PDP and an XACML PDP may use XACMLResponse to return authorization decisions in response to an XACMLAuthzDecisionQuery.
Then, this profile shows the use of SAML for use in requesting, responding with, storing and transmitting XACML policies. This category includes four new SAML extensions; XACMLPolicyStatement, XACMLAssertion, XACMLPolicyQuery and XACMLResponse. In an XACML system, XACMLPolicyStatement may hold XACML policies for storage or transmission and XACMLAssertion may hold XACMLPolicySatement instances for storage or transmission. And a PDP or other application uses XACMLPolicyQuery to request XACML from a PAP. Also PAP uses XACMLResponse to return policies in response to an XACMLPolicyQuery.
Finally, this profile details the use of XACMLAssertion instances as advice in other Assertion. This category consists of XACML Advice, which is a new SAML extension element in this profile that may be used for including XACMLAssertion instances as advice in another XACMLAssertion, and XACMLAssertion which is a new SAML extension element that may be used to hold on XACMLAdvice instance along with SAML Statement or XACML extension Statement instance.
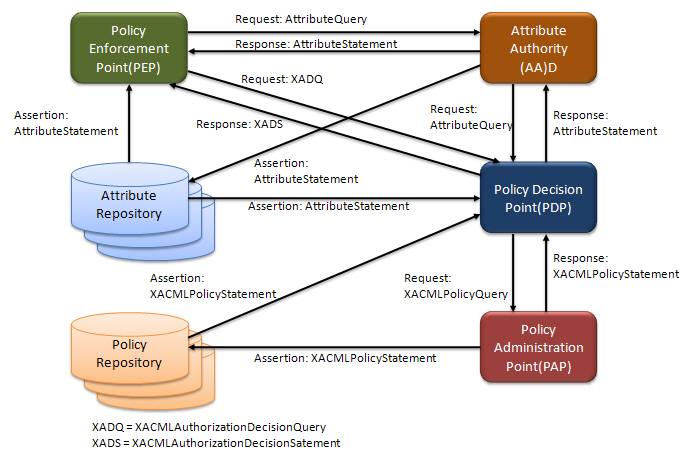
Figure 5 describes the XACML use model and the messages that can be used to communicate between the various components. Statements are carried in SAML or XACML Assertions, and Assertions are carried in SAML or XACML Responses. Not all components or messages will be used in every implementation. Next subsection shows the practical example of this model.
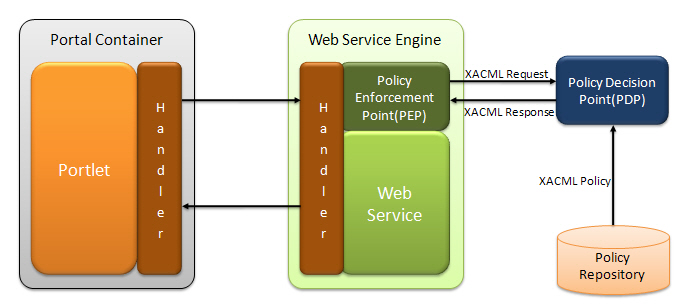
The steps of communication between Portal and Web services are described in detail as follows:
Focusing on access control we represent SAML and XACML which are developed by OASIS. SAML is an XML-based framework for exchanging authentication and authorization data. Because SAML has much strength such as platform neutrality, loose coupling of directories, improved online experience for end user, reduced administrative costs for service providers and risk transference. Also SAML is being applied in Web Single Sign-On, Attribute-Based Authorization, and Securing Web Services.
XACML defines XML files which contains access control policy and access control decision request/ response. Policy Decision Point (PDP) looks at the request from Policy Enforcement Point (PEP) and finds some policy applying to the request from Policy Administration Point (PAP) and returns the response about whether access should be granted to PEP.
XACML defines the content of Request/Response messages but does not define protocols or transport mechanisms, which SAML provides by defining schemas for use in requesting and responding with various types of security assertions. This SAML/XACML based access control is a very powerful and practical solution for dynamic and large-scale application domain because it is easier to change and maintain policies. So it can extend the authentication and authorization mechanism within a portal to external Web services.
| [Candolin07] | Candolin, Catharina, "A Security Framework for Service Oriented Architectures", Military Communications Conference, 2007. MILCOM 2007. IEEE, 29-31 Oct. 2007, pp.1-6 http://ieeexplore.ieee.org/document/4455332/ |
| [Singhal07] | Singhal , Anoop, "Web Services Security: Challenges and Techniques" policy, Eighth IEEE International Workshop on Policies for Distributed Systems and Networks (POLICY'07), 2007, pp.282 http://www2.computer.org/portal/web/csdl/doi/10.1109/POLICY.2007.50 |
| [Madsen05] | Madsen, Paul, et al., "SAML V2.0 Executive Overview", OASIS Committee Draft, 12 April 2005 http://www.oasis-open.org/committees/download.php/13525/sstc-saml-exec-overview-2.0-cd-01-2col.pdf |
| [Ragouzis08] | Ragouzis, Nick, et al., "Security Assertion Markup Language (SAML) V2.0 Technical Overview", Committee Draft 02, 25, March 2008, http://www.oasis-open.org/committees/download.php/27819/sstc-saml-tech-overview-2.0-cd-02.pdf |
| [Sun] | "Sun's XACML Implementation", July 2004, http://sunxacml.sourceforge.net/guide.html |
| [Moses05] | Moses, Tim, et al., "eXtensible Access Control Markup Language(XACML) Version 2.0", OASIS Standard, 1 Feb 2005, http://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf |
| [Periorellis07] | Periorellis,Panos , "Securing Web Services: Practical Usage of Standards and Specifications", Idea Group Inc(IGI), 2007. http://books.google.com/books?id=zX2N7fWTJOUC |
| [YIN07] | Yin, Hao, et al., "A SAML/XACML Based Access Control between Portal and Web Services", Data, Privacy, and E-Commerce, 2007. ISDPE 2007. The First International Symposium on, Nov. 2007, pp 356-360 http://ieeexplore.ieee.org/document/4402710/ |
| [Anderson05] | Anderson, Anne, et al., "SAML 2.0 profile of XACML v2.0", OASIS Standard, 1 Feb 2005 http://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-saml-profile-spec-os.pdf |
| [Jamil08] | Jamil, Ejaz, et al., "What really is SOA. A comparison with Cloud Computing, Web 2.0, SaaS, WOA, Web Services, PassS and others", SOALIB, 12 Dec 2008. http://soalib.com/docs/whitepaper/SoalibWhitePaper_SOAJargon.pdf |
| [Google] | SAML Single Sign-On (SSO) Service for Google Apps, http://code.google.com/apis/apps/sso/saml_reference_implementation.html |
| AA | Attribute Authority |
| B2B | Business-to-business |
| CORBA | Common Object Request Broker Architecture |
| DCE | Distributed Computing Environment |
| GSA | General Services Administration |
| IDP | General Services Administration |
| J2SE | Java Platform Standard Edition |
| ID-WSF | Identity Web Services Framework |
| LDAP | Lightweight Directory Access Protocol |
| OASIS | the Organization for the Advancement of Structured Information Standards |
| PAP | Policy Administration Point |
| PDP | Policy Decision Point |
| PEP | Policy Enforcement Point |
| PIP | Point Information Point |
| SAML | Security Assertion Markup Language |
| SOA | Service Oriented Architecture |
| SOAP | Simple Object Access Protocol |
| SP | Service Provider |
| SSL | Secure Sockets Layer |
| SSO | Single Sign-On |
| TLS | Transport Layer Security |
| WSS | Web Security Service |
| XACML | eXtensible Access Control Markup Language |
| XKMS | XML Key Management Specification |
| XML | eXtensible Markup Language |
| XSLT | eXtensible Markup Language |
Last Modified: April, 19, 2009
This and other papers on latest advances in network security are available on line at http://www.cse.wustl.edu/~jain/cse571-09/index.html
Back to Raj Jain's Home Page