| Mark A. Shasteen [mark.shasteen@sbcglobal.net] (A survey paper written under guidance of Prof. Raj Jain) |
Download |
Abstract- As business, entertainment, and research becomes more mobile, and people require constant access to information, the need for battery operated means of generating and accessing information keeps increasing. A major consideration in designing these networks is energy efficiency and low power consumption. This survey paper provides a comprehensive look at new and emerging energy efficient wireless protocols. The benefits of each protocol are given, and then the different ways of conserving energy are compared.
Key Words- Energy efficient protocols, energy efficiency, energy aware, low power, efficient wireless, sensor networks
Wireless networks have had significant impact on the world. Specifically, telecommunication wireless networks have made significant impacts as far back as World War II [Wikipedia01]. As these networks become more mobile, and move into remote locations, the need for battery operated devices running energy efficient wireless protocols increases. Energy densities of batteries have only doubled every 5 to 20 years, depending on the particular chemistry of the battery. Prolonged refinement of any given chemistry yields diminishing returns. For this reason, energy conservation in wireless protocols will continue to be a critical issue in the foreseeable future [Brinza06].
Wireless networks that are commercially available today have protocols that included designs to increase power efficiency. Both WiFi and Bluetooth are widely available in commercial products today. Many of the newer energy efficient protocols take concepts utilized in these protocols and improve them or tweak them for networks designed for a slightly different purpose.
A category of wireless networks where energy efficient protocols are a major interest is wireless sensor networks (WSN). WSNs are a relatively new emerging research area with many applications in environmental monitoring, precision agriculture, military, home automation and security, context-aware personal assistants, and medical monitoring [Pianegiani08][Kim05]. WSNs consist of many randomly scattered and possibly moving sensor nodes. These nodes are generally powered by non-rechargeable limited power batteries so efficient use of power is key to these networks.
This paper gives a brief explanation of many new and emerging wireless protocols. The energy efficiency techniques used by these technologies are given. The benefits of the techniques are given as well as the costs. An explanation of the environment a particular protocol was designed for is given where appropriate.
The rest of this paper is organized as follows: Section 2 briefly describes the energy efficient aspects of protocols that are commercially available today. Section 3 expands upon the many new protocols being studied for efficiently using power in WSNs. Section 4 lists the energy efficiency techniques and categorizes the different protocols that use the given techniques, and the paper concludes with the summary in section 5.
All wireless networks benefit from lower energy usage. Each new generation of wireless product expands the accessibility of telecommunication networks. Many of these new products are lightweight mobile devices that need to conserve power. WiFi and Bluetooth are two protocols that are widely used by portable electronics. Both have certain parts of their protocols designed to reducing power consumption.
Wireless local area networks (WLAN) have now been around for a few decades. Early WLANs consisted of proprietary protocols which precluded interoperability between networks. Wi-Fi is a certification based on the IEEE 802.11 standard that guarantees interoperability between certified components. The majority of laptops and PDAs now come with Wi-Fi as a standard feature [Smith05]. Two methods in which Wi-Fi devices reduce energy consumption are reducing retransmissions and entering sleep mode when access to the network is not needed [Smith05].
When a device wants to transmit, it uses an exponential backoff algorithm to determine how long it will wait before attempting to transmit. Using a random delay and exponentially increasing the range of the random delay decreases the probability that two devices will transmit at the same time. Wi-Fi devices also use short control packets called Request to Send and Clear to Send before transmitting the longer data packets. The control packets reduce collisions because of their small size and also because they allow other devices to know the wireless medium is being used even if they can't hear the whole data transmission. Although the data packets are larger than the control packets, they are still relatively small packets to keep retransmission costs to a minimum [Brenner97].
If a device is not currently sending or receiving data, it can enter sleep mode. In sleep mode the device can conserve power without loosing information. The sleeping device will periodically listen to network access point beacon frames. The access point will buffer data for the sleeping devices. The beacon frames let the sleeping devices know which ones need to wake up to receive the buffered data [Brenner97].
Bluetooth is a wireless radio technology for low power, low cost, short range communication. Bluetooth uses time division duplexing (TDD) where a master node controls media access through polling slave nodes. Both types of nodes only communicate in their pre-assigned time slots. This avoids communication collisions and the need to resend data due to those collisions. Bluetooth also incorporates low duty cycle modes. A slave node may enter a sniff, hold, or park state. In the sniff state, the node "sleeps" for a predetermined amount of time and periodically wakes up for data transmission. In the hold state, the node again sleeps for a predetermined time, but there is no data transfer while in the hold state. If the node does not need to communicate, the master node may put the slave node into the park state. In the park state the node relinquishes its active address in the network so it may be used by another node [Wells05].
Media access control is an essential part of wireless communication networks. TMMAC increases throughput and lowers power consumption of networks like WiFi that are based on the IEEE 802.11 standard. TMMAC focuses on incorporating both the advantages of multiple channels and TDMA into a MAC design with low overhead for increased throughput and low energy consumption. TMMAC is designed for a network where each node is only equipped with a single half-duplex radio transceiver. Having only one radio transceiver keeps product prices low and consumes less power. Most 802.11 devices are only equipped with single half-duplex radio transceivers [Zhang07].
TMMAC requires time synchronization. Time is divided into two fixed periods: an Ad Hoc Traffic Indication Messages (ATIM) window followed by a communication window. During the ATIM window, four control packets: ATIM, ATIM-ACK (ATIM-Acknowledgement), ATIM-RES (ATIM-Reservation), and ATIM-BRD (ATIM-Broadcast) are used on one default channel for communication negotiation. Communication in the ATIM window is the contention based scheme of 802.11 Distributed Coordination Function protocol [Zhang07].
The Channel Usage Bitmap (CUB) and the Channel Allocation Bitmap (CAB) are two data structures used in TMMAC. The CUB represents the current usage information of one channel. Each node keeps track of a CUB for each available channel. The CAB is used to negotiate changes to the CUB. Nodes that do not negotiate sending or receiving time slots in the CUBs put themselves into a sleep mode until the next cycle [Zhang07].
For unicast communication, the ATIM, ATIM-ACK and ATIM-RES control packets are used in the ATIM time period. First the node that has information to send uses an ATIM packet to tell the receiving node the current CUB for three channels that have the lowest usage. It also tells the receiving node how much data it needs to send. The receiving node compares the sending nodes CUBs with its own CUBs and sends back an ATIM-ACK with both the updated CUBs and the CABs that the sending node should use. Finally the sending node sends out the ATIM-RES confirming the new CUBs and CAB. All nodes within listening distance of either the sending or receiving node update their CUBs with the negotiated timeslots [Zhang07].
It is more difficult to allocate time slots for broadcast packets, since no channel in that time slot can be previously allocated for use. To alleviate that problem, if a node has both unicast and broadcast packets to send, it negotiates the broadcast packets first. Also, smaller backoff windows are used for broadcast negotiation. The ATIM-BRD packets are used for broadcast communication. The sending node randomly selects available time slots and sends out the CUBs and CABs it plans on using for the broadcast. The nodes in the vicinity of the sending node update their CUBs based on the ATIM-BRD packet [Zhang07].
To increase the throughput and energy conservation even further, TMMAC has each node dynamically adjust its ATIM window size. When the network is not saturated, the ATIM window is shortened to save energy. When the network is saturated, the ATIM window size increases to allow more successful communication negotiations. To avoid ATIM control packet collisions with data communication, the default channel is never used for communication before a maximum ATIM window size time has passed. However, the other channels can be used for communication during this time if both the sending and receiving nodes have ATIM window sizes smaller than the maximum ATIM window size [Zhang07].
TMMAC exploits the advantages of multiple channels and TDMA to achieve high throughput in an efficient way. It also supports highly power-efficient data broadcast. TMMAC has been shown to achieve up to 113% high communication throughput while consuming 74% less per packet energy over other state-of-the-art multi-channel MAC protocols that use single half-duplex radio transceivers [Zhang07].
Wireless Sensor networks consist of sensors placed in remote areas to collect data and send it back to a base station. Due to the fact that WSNs generally have battery operated sensor nodes, there is a lot of focus on finding the best energy efficient protocols for these networks. The part of the node that consumes the most energy is often the radio module [Pianegiani08]. Studies reveal that energy wastage occurs mainly from collision, overhearing, control packet overhead and idle listening [Lin05].
One of the challenges in designing a wireless sensor network is that sensors are organized into a multihop wireless network that must be able to function properly for long periods of time on limited power supplies. Many researchers have suggested deploying different types of nodes into the network as a way to solve this problem. In the two-layered heterogeneous sensor network, two types of nodes are deployed: the basic sensor nodes and the cluster head nodes. The basic sensor nodes perform the sensing task. They are simple nodes and have limited power supplies. The cluster head nodes organize the basic sensors around them into a cluster that only communicates with the cluster node. They are much more powerful and focus on communications and computations [Zhang08]. Figure 1 shows an example of a two-layered heterogeneous WSN.
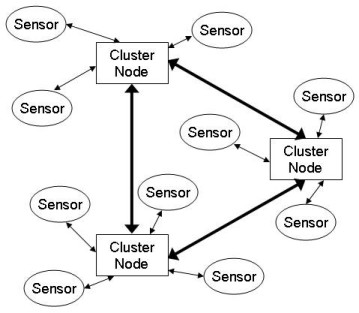
Figure 1. Two Layer Heterogeneous WSN
Having a two layer sensor network can also increase energy efficiency by using the cluster nodes as central media controllers. Contention-based distributed MAC protocols are robust and require no central controller, however, from the energy point of view, they are not the most efficient MAC for WSNs. Having a central controller poll the sensor nodes reduces idle listening and resending due to collisions. It also reduces the protocol overhead used in collision avoidance. It should be noted that central controller polling schedules do not work well in environments where the network layout changes rapidly. The cluster nodes should only be used as media controllers in applications where the environment and sensors are relatively static [Zhang08].
As the two layer heterogeneous sensor network showed, sensor data can be fused at a cluster node before being sent to the base station. Sensors are sometimes placed in locations that are vulnerable to malicious attackers. Information assurance of the data fusion process is very important to be sure the sensor data has not been compromised. One solution proposed for information assurance is witness-based data fusion. In witness-based data fusion a randomly chosen sensor node votes to confirm the correctness of the fusion data. With direct voting in sensor networks, the witness node transmits the vote directly to the base station. This method of voting performs better in terms of information assurance, overhead and delay than having the votes transmitted to the base station by the cluster node [Pai08]. Figure 2 shows a WSN using direct voting.
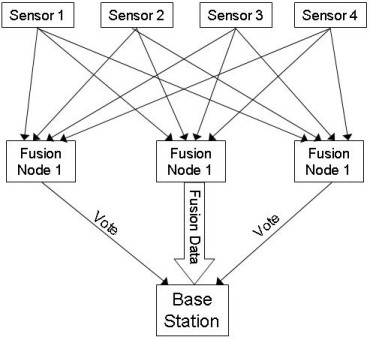
Figure 2. Direct Voting WSN
In the direct voting scheme, only one copy of the correct fusion result needs to be sent to the base station. Witness nodes only transmit when they disagree with the fusion result sent to the base station. They remain silent when they agree with the transmitted fusion result. The base station can terminate the voting process when the threshold of agree or disagree votes has been received [Pai08]. All of these features reduce the amount of overhead data that is transmitted. Early termination of the voting process and the silent assent vote reduce the number of nodes that transmit.
Many WSNs adopt a centralized computational approach where the sensor nodes acquire measurement information and send it to the base stations without executing any preprocessing. The base stations then process the information. A different approach is to have the sensor nodes exploit their computing and memory capabilities to locally process the acquired information. As opposed to sending the entire stream of raw data, the sensor nodes select a subset of features from the detected signals, classify those features, then send only the classification results to the base station. The sensor nodes have limited energy, memory, and processing capabilities, so the classification algorithm has to be a high-accuracy low complexity algorithm such as maximum-likelihood estimation, k-nearest neighbor, or support vector machines.[Pianegiani08].
Density of deployment in sensor networks can be very high, leading to a lot of redundancy. One approach to saving energy is to turn off redundant nodes. The sensors should schedule their sensing and sleeping times to minimize the overall awake time of the sensors while ensuring that the entire network neighborhood is completely covered. When choosing which redundant node to turn off, the scheduling algorithm should choose the node with the lowest energy to increase the overall lifetime of the sensor network[Kalidindi05].
A good way to ensure that the entire network neighborhood is covered is to divide the whole sensing area into a virtual grid. The distance between grid points should be small enough that when the sensor node schedules cover these grid points, they also cover the whole sensing area. Assigning the sensing schedule based on all the sensors that cover a single grid point versus how many grid points a sensor covers allows the schedule to balance energy consumption in the nodes[Kalidindi05].
Two simple methods for disseminating information in WSNs are flooding and gossiping. Flooding has a high energy cost. Randomly gossiping achieves energy efficiency, but disseminates information slowly and does not always guarantee data delivery. Two protocols that can achieve both energy efficiency and a high querying success rate with fast information disseminating are the quorum scheme and the home-agent scheme. These protocols use three types of messages: ADV - advertisement of newly sensed data (includes node location information), REQ - request for data (includes node location information), and DATA - the actual data message. The purpose of the quorum scheme and the home-agent scheme is to produce a high probability that both the ADV and REQ messages will meet at a rendezvous node without using any type of flooding or broadcasting [Liu06].
In the quorum scheme, all ADV messages are propagated north and south creating a vertical line of nodes that receive the ADV message. Similarly, all REQ messages are propagated east and west through the network creating a horizontal line of nodes that receive the REQ message. Once the horizontal and vertical messages meet at node, then the communication route can be established to transfer the data. To ensure the messages do not stop at local minimums or maximums, the protocol must incorporate a recovery scheme when a receiving node can no longer forward a message in the correct direction. One way to address the local min or max problem is to have the receiving node forward the message to its neighbor that has the largest clockwise angle formed from the line created from the previous transmission. The transmissions stop when a REQ meets an ADV, or a node receives the same message twice (Figure 3). The quorum protocol does not guarantee successful information dissemination in all cases, however it does create at least one rendezvous in most cases [Liu06].
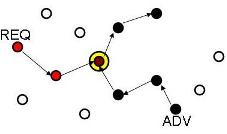
Figure 3. Quorum Scheme Routing
In the home-agent scheme, the sensor nodes need to know the location of the center of the network. The node or nodes located at the center of the network act as the home-agent. All ADV and REQ messages are sent to the center of the network. This method of routing also needs a recovery scheme to avoid getting stuck at local minimums. The home-agent scheme imposes heavy communication load on nodes near the center of the network [Liu06].
To achieve long lifetime in WSNs, the radios need to have low duty cycles of operation. Reducing duty cycle can often lead to performance degradation in throughput and latency. One way to reduce duty cycle while still achieving good throughput with low latency is to use Convergent MAC (CMAC). CMAC begins with an unsynchronized duty cycle using anycast and converges to a synchronized unicast once an optimal forwarding node is found [Liu07].
In the beginning unsynchronized anycast portion of CMAC, a node that wants to transmit uses aggressive RTS where the "wakeup" packets are separated by fixed short gaps. This allows the receiving node to send back a Clear To Send (CTS) packet during the gap allowing the transmitting node to send the data immediately. In order for the receiving node to listen for a very short period while still ensuring that it does not only listen during the aggressive RTS gap, it can separate two short listening cycles by a fixed gap a little longer than the RTS gap. All nodes able to receive the aggressive RTS transmission may reply with CTS, so the receiving nodes prioritize their CTSs based on their distance from the final destination. The node closest to the final destination end up forwarding the packet [Liu07].
Once the best node for forwarding a packet has been found, the transmitting node can converge from anycasting its packets to all nodes, to unicasting to the node it knows is route optimal. When the transmitting node intends to converge from anycast to unicast, it then synchronizes its schedule with the receiver. Both nodes maintain the synchronized schedule until a certain duration without traffic has passed [Liu07].
In the Pattern-MAC (PMAC) protocol, the sleep-wakeup schedules of the sensor nodes are adaptively determined. A nodes "pattern" is its tentative sleep-wake up plan where a 0 indicates sleep and a 1 indicates awake. At first nodes exchange their patterns for a period of communication. Then nodes decide their actual sleep-wake up schedule based on their pattern and the patterns of their neighbors. If a nodes pattern was 1 then it needs to always set its schedule to 1 in case another node needs to transmit to it. If the node does not sense any of its neighbors trying to communicate with it, it can sleep for the remainder of the frame. If a nodes pattern was 0 but it needs to transmit data to a node whose pattern was 1, then the node can change its schedule to 1 and transmit the data quickly to increase throughput. Nodes can quickly increase the number of zeros in their pattern during periods of light communication to conserve energy. How quickly a node adds zeros to its pattern can be optimized for its intended application [Zheng05].
Many efforts on optimizing power consumption have concentrated on routing protocols. Another important factor in sensor network energy conservation is total network lifetime. DEEPS increases sensor network lifetime by using distributed algorithms for continuous and event-driven sensor network models. Instead of deciding which nodes to put to sleep based on the individual nodes battery power, DEEPS determines the total battery power that is left covering a given target within the network. If a target is found to have the lowest cumulative battery power left to cover it, then it is covered by a single sensor with the largest battery power. If by turning off the other sensors covering that target, some other target becomes uncovered, then the sensor who's remaining targets have the highest total battery power left covering them, stays on to cover the uncovered target. This scheduling method can almost double the total network lifetime compared to algorithms that only look at individual sensor's battery power [Brinza06].
Now that multiple protocols have been discussed, the different ways of increasing energy efficiency will be looked at in more detail. The major areas contributing to energy efficiency are reducing bits, reducing duty cycle, reducing collisions and resends, reducing transmit power, and reducing idle listening. Reducing computations and increasing network life through even energy consumption will also be looked into, although they do not directly conserve large amounts of energy like the other techniques discussed. Different protocols will be compared and contrasted with respect to the different ways of increasing energy efficiency. Many of the techniques discussed fit into multiple efficiency types.
Reducing the number of bits sent across the wireless network reduces transmit power as well as listening power. TMMAC reduces overhead by dynamically adjusting the window for control messages. Using a two-layer network with a central controller that polls the other network nodes eliminates bits used in collision avoidance overhead. Direct voting for data assurance reduced the number of overhead bits by utilizing passive assent voting, early vote termination, and a single fusion result transmission by an uncompromised node. Classification of signals in sensor networks substitutes low power processing for high power data transmission in sensor networks. CMAC reduces bits by eliminating the need for the overhead of duty cycle synchronization.
Many protocols reduce power by having nodes enter a low duty cycle sleep mode. Sleep modes conserve power when nodes do not need to send and receive data. CMAC reduces duty cycle by having an unsynchronized anycast method of waking up surrounding nodes for communication. PMAC reduces duty cycle using sleep-awake patterns of all nodes in a neighborhood to optimize the duty cycle schedules of those nodes.
Collisions waste power in wireless networks. Some protocols reduce collisions while others completely eliminate them. The two layer heterogeneous network with a central media controller eliminates collisions by only allowing nodes to communicate after they have been polled. Bluetooth uses master and slave nodes the same way.
A wireless protocol can conserve power by reducing the number of nodes that transmit data. In the direct voting for data assurance protocol, silent assent voting and early vote termination are used to reduce the total number of communicating nodes. In a sensor network, the number of communicating nodes can be reduced by turning off redundant nodes. The quorum and home-agent schemes can be used to reduce the number of nodes needed to disseminate information. After finding an optimal route, CMAC converges from anycast where multiple nodes are issuing CTSs to the transmitting node, to unicast where only the transmitting and receiving nodes communicate.
Protocols can reduce transmit power in two ways. One is knowing exactly where the two nodes are located that need to communicate so that the transmit power needed for communication can be minimized. The other is having most of the nodes communicate through relay and mesh networks to reduce the transmit distance. In two-layer networks, nodes can transmit short distances to data sinks or cluster nodes. The cluster node can then send the data over a larger distance conserving the power of the smaller nodes.
Idle listening wastes a lot of energy in wireless networks. Idle listening can use as much energy as actually receiving data. The example of power consumption of the Mica2 Mote sensors is shown in table 1 [Seongcheol05]. Protocols can reduce power consumption by minimizing idle listening. CMAC reduces idle listening by anycasting an aggressive RTS packet to wakeup surrounding nodes. The receiving nodes in CMAC only need to listen for two short periods. PMAC reduces idle listening by using sleep-awake patterns to determine duty cycle schedules.
| Radio State | Power Consumption (mW) |
|---|---|
| Transmit | 81 |
| Recieve | 30 |
| Idle Listening | 30 |
| Sleep | 0.003 |
The two layer network with a central media controller reduces idle listening by eliminating the need for nodes to constantly monitor for possible data packets destined for them.
Computation does not use as much energy as transmitting and receiving in wireless networks. The energy necessary to perform 3000 instructions is comparable to the energy needed to send 1 bit across 100m by radio [Brinza06]. However, some networks use nodes with limited computing ability. A two layer sensor network can use a cluster node to perform heavier computations while leaving only the sensing task to the smaller sensor nodes. Maximum-likelihood estimation, k-nearest neighbor, and support vector machines are high-accuracy low complexity algorithms that can be used to classify data so only the classification results need to be sent across the network. Minimizing computations needed for energy efficient protocols can make the implementation of those protocols possible.
Even energy consumption is not a direct energy saver. It does however increase the total life span of a wireless network that operates on limited power supplies. Maximizing the lifetime of the individual wireless nodes can keep the entire network operating more efficiently by eliminating the need to compensate for low coverage areas. DEEPS [Brinza06] increases sensor network lifetime by deciding to turn off nodes based on the total battery power left for all nodes covering a target. The cost for increasing total network lifetime is often increased transmit power and overhead to coordinate schedules between all the neighboring nodes.
In conclusion, if energy efficiency is a major component in a wireless network design, then many new protocols can be examined to aid in the networks design. However, these energy efficient designs may increase the initial hardware cost of the network. Some designs, like TMMAC, focus on both keeping hardware costs and power consumption low, but even TMMAC has to trade some throughput for the overhead needed to conserve energy. Additionally, some energy efficient protocols require more than one type of node so that some nodes can be extremely energy efficient devices while others bare a larger load. These "cluster" or "sink" nodes will need to have more robust power supplies. The benefits and costs of each type of protocol need to be researched to see which concepts are best applied to any given network topology.
| ADV | Advertisement |
| ATIM | Ad Hoc Traffic Indication Message |
| ATIM-ACK | ATIM-Acknowledgement |
| ATIM-BRD | ATIM-Broadcast |
| ATIM-RES | ATIM-Reservation |
| CMAC | Convergent MAC |
| CAB | Channel Allocation Bitmap |
| CTS | Clear To Send |
| CUB | Channel Usage Bitmap |
| DEEPS | Deterministic Energy-Efficient Protocol for Sensor Networks |
| IEEE | Institute of Electrical and Electronics Engineers |
| MAC | Media Access Control |
| PMAC | Pattern-MAC |
| REQ | Request |
| TDD | Time Division Duplexing |
| TDMA | Time Division Multiple Access |
| TMMAC | TDMA Based Multi-Channel MAC |
| WLAN | Wireless Local Area Network |
| WSN | Wireless Sensor Network |
Last modified: June 25, 2008
This and other papers on latest advances in wireless networking are available on line at http://www.cse.wustl.edu/~jain/cse574-08/index.html